In contrast to Open System Authentication, in Shared Key Authentication the key that would be used for data security is used to authenticate the WLAN station. The Below steps are followed in Shared Key Authentication
- Authentication request sent by WLAN (802.11) STA to Access Point
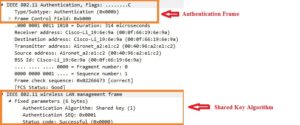
- AP sends a challenge text to 802.11 STA (in cleartext)

- Station encrypts the challenge text with its encryption key and transmits the encrypted text to AP

- AP decrypts the challenge text and if challenge text decryption is successful – sends authentication success message to the 802.11 station

Flaw in Shared Key Authentication
There is a serious flaw in Shared Key Authentication. The Challenge text and the encrypted text are both sent out on air. It is a simple mathematical operation to obtain the key used in encrypting the challenge text as both the encrypted and clear text are available to anyone who is sniffing the channel medium.
In this respect, Open System Authentication provides more security than Shared Key Authentication since the WLAN station can still send encrypted data to the Access Point if both the Access Point and the 802.11 WLAN station have a pre-configured key