PMKID stands for Pairwise Master Key Identifier. It is a unique identifier that is generated during PMK security association for a specific AP-Client.
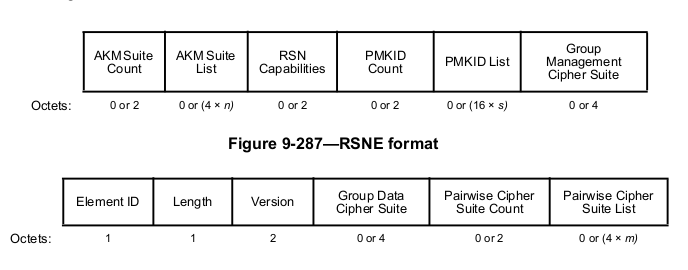
The PMKID computation is basically a truncate-128 operation on HMAC-SHA-1/HMAC-SHA-256/HMAC-SHA-384 hashing. The different ways of obtaining PMKID depends on the cipher suite selected for RSN. Refer section “12.7.1.3 Pairwise key hierarchy” in 802.11-2020 standard document to obtain the formula used. PMKID parameter in the RSNIE is shown below:
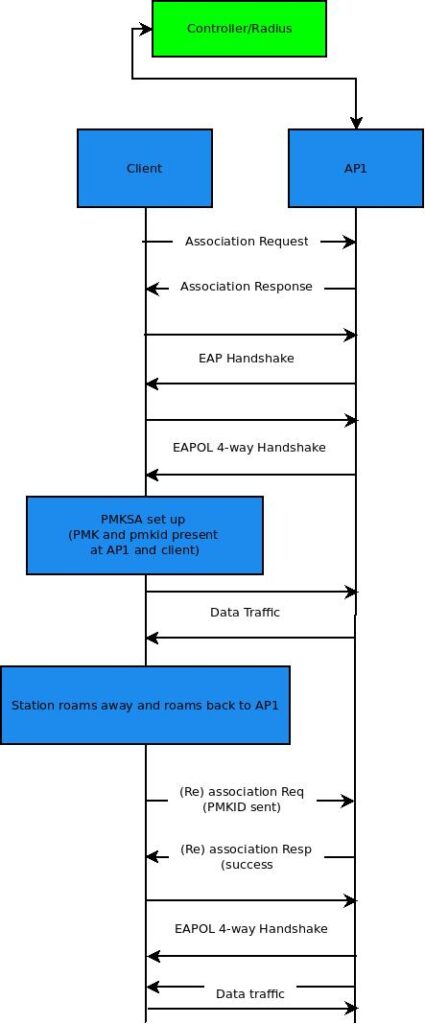
PMKID provides a client the ability to skip the EAP handshake during roam back to a previous AP. When a client connected to an Access point (AP1) roams away from that AP1 and later roams back into the range of AP1, Client can
- Use the cached PMKID for the PMKSA from previous AP1 connection in the (Re)association request to AP1
- If the PMK security association for the specific PMKID sent in the (Re)association request is still valid
- AP1 will try and generate the PTK and other keys by following the EAPOL 4-way handshake immediately and skip the 802.1x EAP handshake
- This allows the client to roam back to AP1 in a much shorter duration as it does not to reach the Radius server for EAP handshake
- If the PMKID sent in (Re)association request does not map to any PMKSA at the AP side (as the PMKSA has already timed-out), then the client has to perform a full EAP-handshake
- This mechanism to cache the pmkid for a specific connection and later re-use the same in an attempt to have faster roam connectivity to a specific Access Point is termed PMKID caching
Pingback: Opportunistic Key Caching (OKC) | Hitch Hiker's Guide to Learning
Pingback: Pre-Authentication Mechanism in WLAN | Hitch Hiker's Guide to Learning